Automatically validate detection stack,
gain real-time attack surface visibility,
investigate existing risks matching custom threat hunting scenarios,
and prioritize detection procedures to find breaches before adversaries have a chance to attack.

Gain Complete Visibility
98%
Blind spot reduction via an automated ATT&CK data audit
Maximize Efficiency
100X
Better team’s productivity with automated capabilities
Reduce Risk
50%
Faster MTTD & MTTR to eliminate risks of a breach
Drive More Value
60%
Savings in cloud storage costs
Why Attack Detective?
Organizations are struggling with making sense of the vast and diverse pool of data generated by an ever-expanding attack surface and the intricate cyber threat landscape. This is where a solution like Attack Detective steps in as a game-changer.
Limitless Visibility, Breachless Experience
Empowered with Attack Detective, security teams can easily consolidate disparate pools of data stored within on-premises and multi-cloud environments into actionable insights, obtain a heatmap over a selected time period with triggered TTPs, check if the visualized data can be attributed to a relevant attack, and streamline threat hunting procedures by serving a set of prioritized Sigma rules – with all that possible within hours and from a single place.
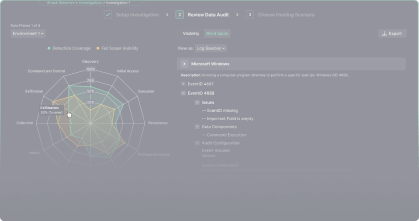
MITRE ATT&CK Data Audit
Validate your detection stack in less than 300 seconds with an automatic read-only ATT&CK data audit to find blind spots in your log source coverage.
Content Selection for Improved SOC Efficiency
Put together a query set that fits your existing data to run an automated scan or validate queries for detection engineering that can be used in the production environment.
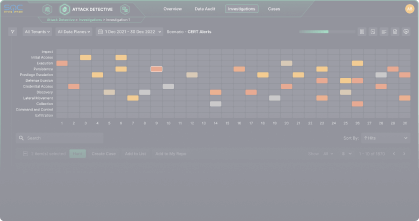
Automated Threat Hunting & Breach Discovery
Scan the environment with custom parameters and dataset to determine the potential attack surface. Quickly filter the results and verify them in your Data Plane to remediate the threat in the least time possible.
Get Started with Attack Detective
Scan your assets for ongoing attacks, see the attack evolution dynamics, get relevant CTI, and detect threats proactively.

1
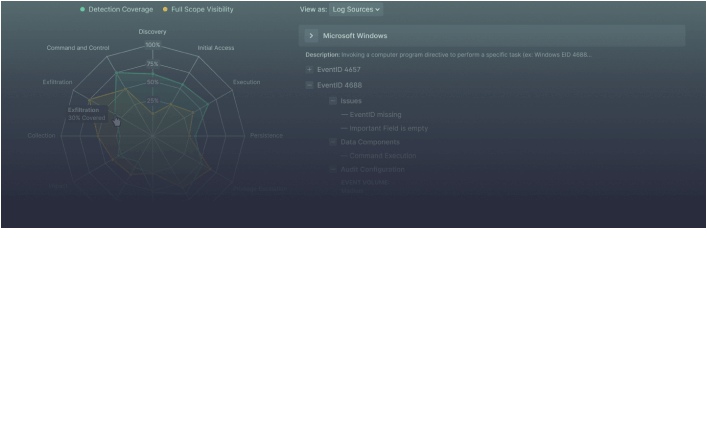
Gain a Comprehensive View of Your Overall Coverage
Dynamically track your detection coverage based on log sources and ATT&CK, identify blind spots, and prioritize areas to focus on for proactive cyber defense.

2
Launch a Scan That Is Customized to Your Security Needs
Run the scan based on the chosen platform and log sources to match the data you have in your defense system with prioritized detection content from SOC Prime’s platform.

3
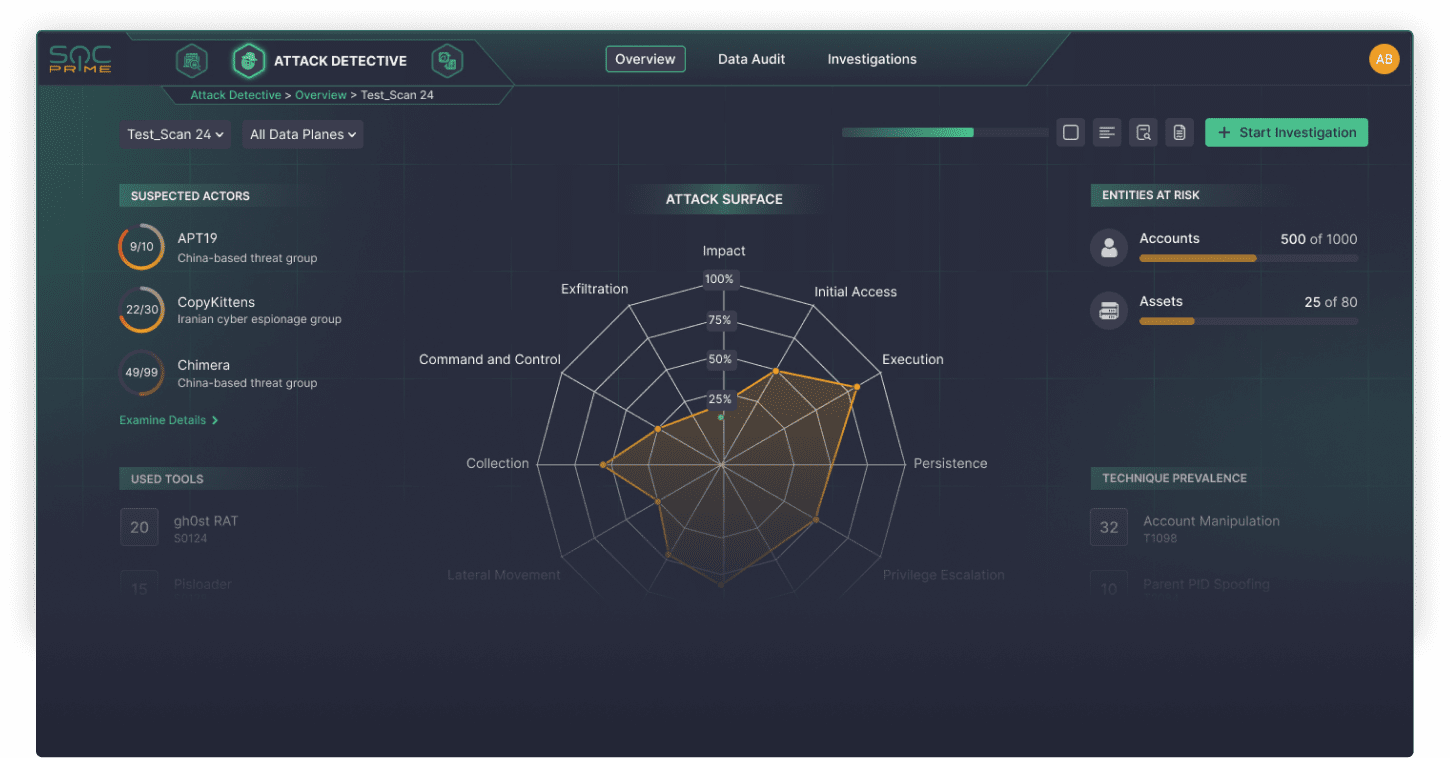
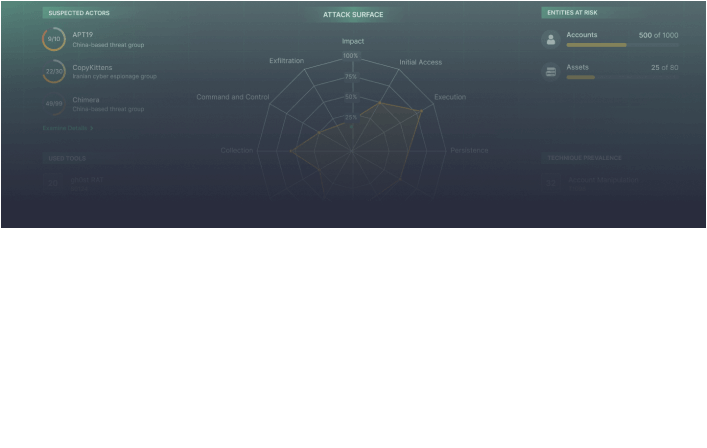
Gain a Snapshot of Your Attack Coverage in Real Time
Explore the outcomes consolidated into the detected ATT&CK techniques along with the impacted assets, services, and accounts. Analyze potential threat actors and adversary tools in use.


4
Drill Down to Analysis Details Mapped to ATT&CK
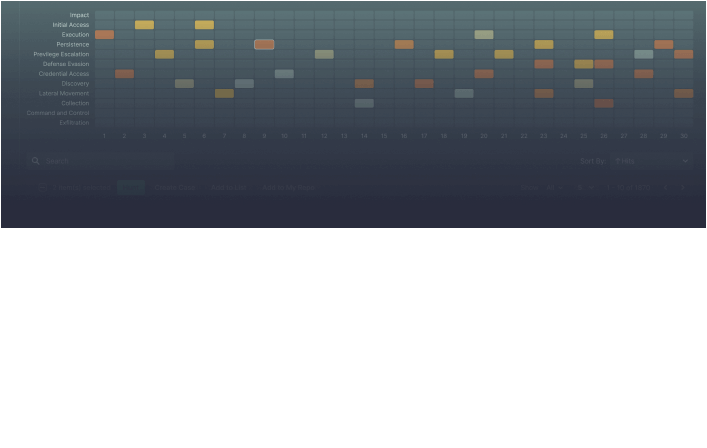
Instantly visualize a heatmap with triggered ATT&CK tactics and techniques and time of access for particular threat actors to find out if they can be attributed to a relevant attack.

5
Deep Dive Into Threat Context Without Alert Generation
Go through the list of relevant Sigma rules with stats of behavior hits along with affected accounts and assets. Rely on feedback from your peers on the rule outcomes.

6
Drill Down into Your SIEM or EDR for In-Depth Investigation
Validate the risks by running selected queries in your SIEM or EDR and
mark the outcomes based on the displayed behavior to prioritize your detection procedures.

Where Trust Meets Resilience
Attack Detective is built on the Zero Trust Architecture (ZTA) milestones enabling organizations to risk-optimize their cybersecurity posture.
Avoid the risk of vendor lock-in
According to the NIST SP 800-207, no vendor can offer a single solution that will provide zero trust, which is highly likely to pose risks for organizations of vendor lock-in. Attack Detective enables cross-platform analytics and vendor-neutral visibility, no matter your tech stack in use.
Keep all the data where it lives
Gain complete visibility based on the organization-specific logs by querying data in its native location. This enables avoiding data duplication or distribution and possible permission inconsistency for the same data across different locations.
Separate data plane from the control plane
Attack Detective fully supports control plane and data plane segregation. Different accounts are used for the Attack Detective policy configuration and for data storage access in different tenants, which excludes the possibility of data transfer between the control plane and data plane.











A Perfect Match for Your Technology
No matter your cloud or on-premises security solution in use, Attack Detective connects industry-leading SIEM, EDR, and XDR technologies in a single place to enable real-time attack surface visibility across the organization-specific environment and streamline threat investigation.
Your Cybersecurity Partner
Rely on SOC Prime to equip your team with the best technology and professional support to stay ahead of cyber attacks.