Unlocking SIEM Excellence:
Splunk Migration & Support Backed
by SOC Prime’s Expertise
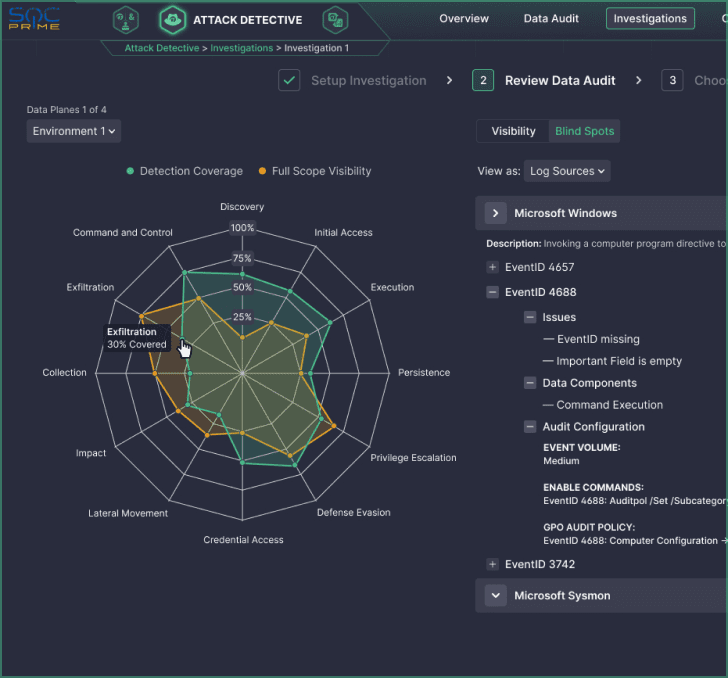
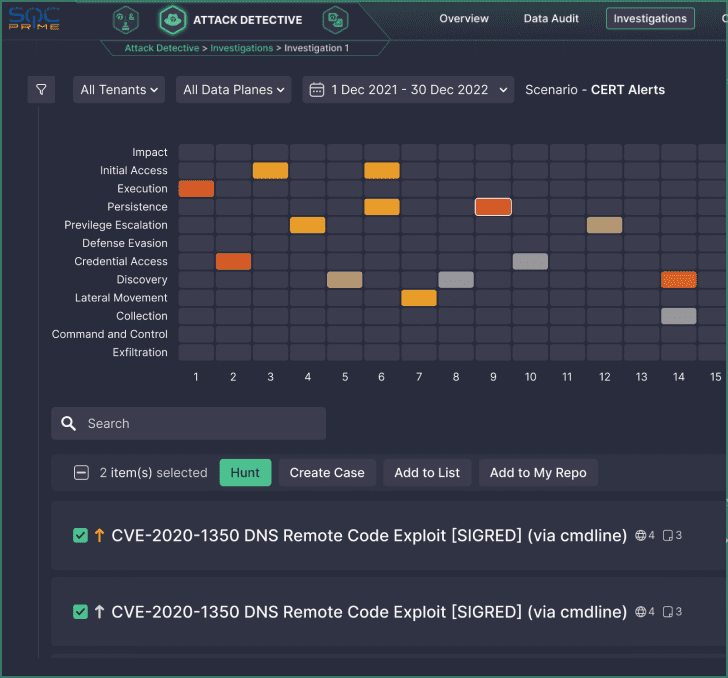
Enhanced Detection Engineering Maturity.
Splunk
Expertise-as-a-Service
Accelerate Splunk Migration to Your Chosen SIEM
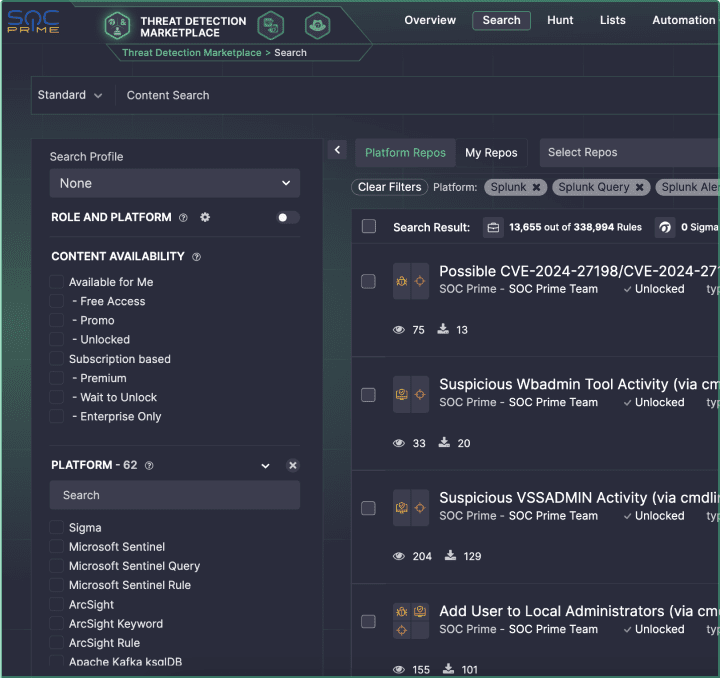
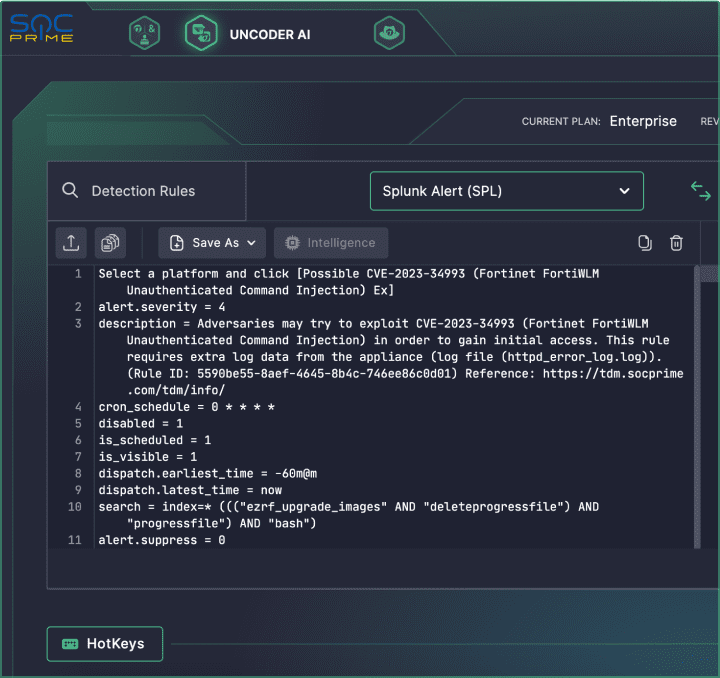
Uncoder AI
The content translation part of SIEM migration requires significant fine-tuning, potentially leading to mismatches with your security use cases and a decrease in detection content quality. Uncoder AI enables automated cross-platform query translation for 11 SIEM, EDR, and Data Lake native languages, including Splunk, to smooth out your migration journey.
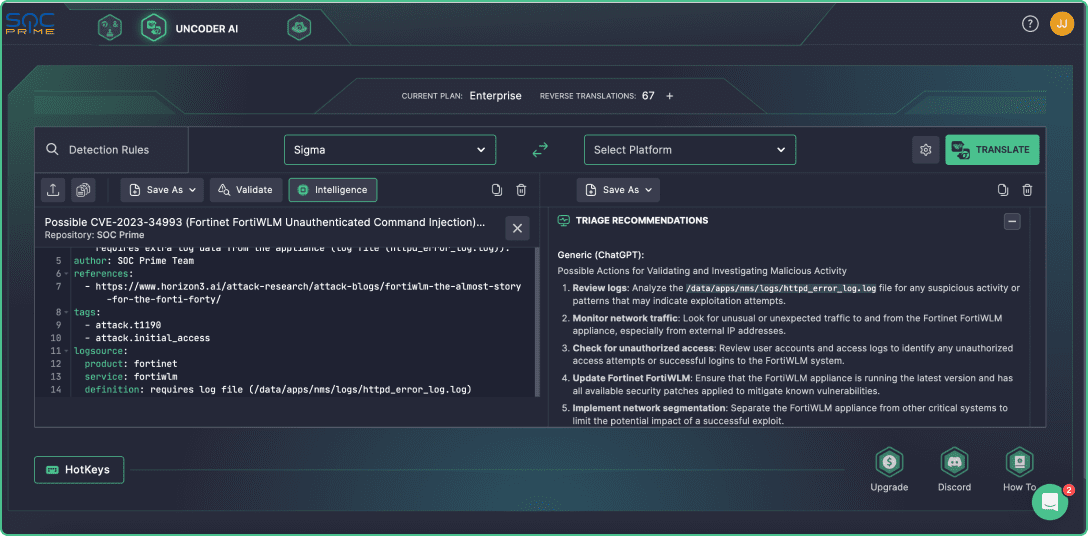
No more code descriptions and metadata saved in separate files. Automatically enrich your translations with tailored CTI, false positive context, triage, and audit configuration recommendations.
No matter what language format you speak, either SPL, KQL, EQL, or other, Uncoder AI supports on-the-fly remapping to your data schema in use for customized deployments.
We keep your secrets, ensuring privacy, security, and intellectual property rights, so you can work with detection code in a fully trusted environment. No data logging and no code sharing with third parties.

Start Now to Secure Your Tomorrow
Safeguard your organization with the best-in-class technology and professional support. Join the world’s first platform for collective cyber defense. Let’s build a secure tomorrow, together.