Monetize Your Threat Detection Content
Join Threat Bounty Program - the world's largest bounty program for cyber defenders. Share your detection rules via the SOC Prime Platform and generate steady income by coding your SOC content while making the cyber world a safer place.
Become Part of the Global Cyber Defense Bounty Program
Develop your own SOC content
Research and code your own actionable detection rules and get them published on the SOC Prime Platform.
Receive regular payouts
Earn regular rewards with a performance-based system that reflects the value of your SOC content to the global community of cyber defenders.
Catch up with the latest trends
Join the SOC Prime Discord community to sync collective efforts aimed at detecting and withstanding critical threats.


Monetize
Your Threat Detection Rules
Go through the skills assessment
Complete the entry submission by sharing your professional cybersecurity profile for the most efficient collaboration.
Contribute your content
Publish your threat hunting rules for rewards, knowing that your authorship rights are honored.
Benefit
Receive ongoing rewards based on the performance of your detections and users’ evaluations.
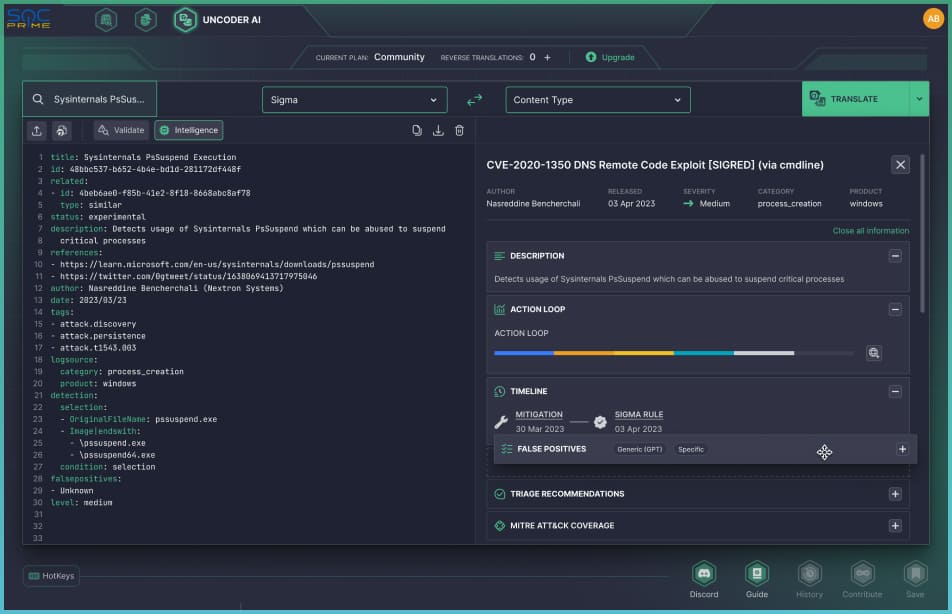
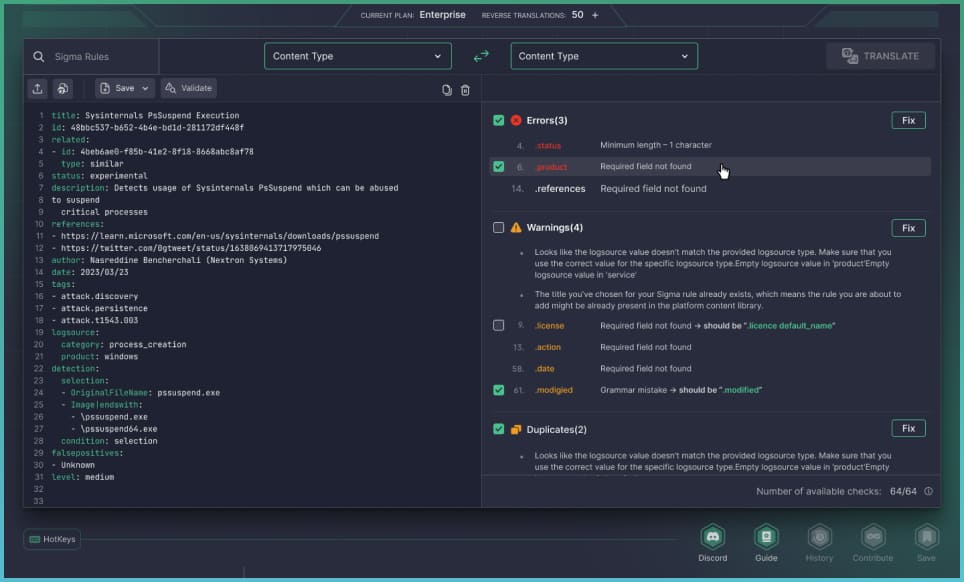
Uncoder AI: All-In-One Tool to Create, Manage & Monetize Your Detection Rules with Threat Bounty Program
Create
Start creating your detection rules for Threat Bounty from scratch directly in Uncoder AI.
Test
Run automated tests in a single click to check rules for common pitfalls.
Verify
Submit your detection rules for review and discuss suggested improvements with SOC Prime experts.
Get Published
You’re all set to get your detections published and receive monthly performance-based rewards.
Modify
Search for your previously published rules and make relevant updates on the fly.
Unlock Opportunities
- Gain More with Threat Bounty
Recurrent payouts
Convert your threat hunting expertise into continuous financial benefits.
Detection engineering portfolio
Code up your cybersecurity portfolio and gain professional recognition by publishing curated content alongside the global 30K+ audience on the SOC Prime Platform.
Continuous tech skills enhancement
Boost your skills in detection engineering and broaden your expertise through collaborative research and content contribution.
Networking and knowledge sharing
Become part of the global community of cyber defenders, join the SOC Prime Discord server, and stay connected.
Community Feedback
Threat Bounty Program:
Frequently Asked Questions
SOC Prime’s Threat Bounty Program is an initiative for crowdsourced detection engineering.
It incentivizes cybersecurity professionals to develop and share actionable threat detection rules.
Program members earn monetary rewards and gain recognition for their contributions,
while organizations benefit from enhanced threat detection capabilities via the SOC Prime Platform.
The Threat Bounty Program is an excellent opportunity to enhance your professional portfolio
and make a meaningful impact on global cyber defense.
For Threat Bounty publications, you can contribute your unique Sigma and Roota rules for detecting specific cybersecurity threats or malicious behaviors. Focus on your original research and innovative and creative detection strategies to enhance threat visibility and response. Contribute to elevating the cyber defense capabilities of organizations worldwide while earning rewards for your expertise.
For your Threat Bounty contributions, we recommend that you focus on developing unique threat detection rules that address specific cybersecurity challenges, for example:
- Behavior-based rules to detect existing and emerging threats
- Detections to spot possible attacks against critical infrastructures, including ICS-capable malware, wipers, and other destructive strains
- Detections for possible vulnerability exploitation addressing technologies actively used across countries, industries, companies, or popular adversary toolkits related to potential state-sponsored attacks.
Please remember that while we encourage creativity and talent development, not all submitted content will be accepted for publication and monetization. Ensure your submissions meet Threat Bounty quality standards to maximize acceptance.
To submit Threat Bounty detection rules, you must be an approved member of the Threat Bounty Program. After gaining membership, you can easily submit your detection content using Uncoder AI on the SOC Prime Platform. This powerful tool acts as your AI-powered co-pilot for efficient threat detection engineering, helping you streamline the process of submission of your Threat Bounty rules. See details here.
SOC Prime thoroughly validates the submitted Threat Bounty rules for both technical accuracy and legal compliance, including IP, before publication. Threat Bounty submissions that do not pass verification are not published. Authors can enhance their detections using Uncoder AI to perform syntax and logic checks and ensure their detection code is ready for review by the SOC Prime Team. During the review, we validate rule syntax, detection logic, and the rule’s resilience against bypass tactics. The content verification process adheres to industry best practices and incorporates continuous feedback from organizations leveraging the SOC Prime Platform.
Threat Bounty rewards are paid monthly to members who actively publish new threat detection rules. Only Threat Bounty content that is successfully published on the SOC Prime Platform qualifies for these rewards, and the amount of your bounty depends on the popularity of your published rules. To maximize your earnings, focus on consistently publishing valuable threat detection rules. Don’t miss the opportunity to monetize your detection engineering expertise and join the Threat Bounty Program today!
If you have questions about Threat Bounty Program and want to learn more about detection content creation and submission, detection code quality validation, performance of Threat Bounty rules, Threat Bounty authors recognition and promotion, feel free to join SOC Prime Discord server.