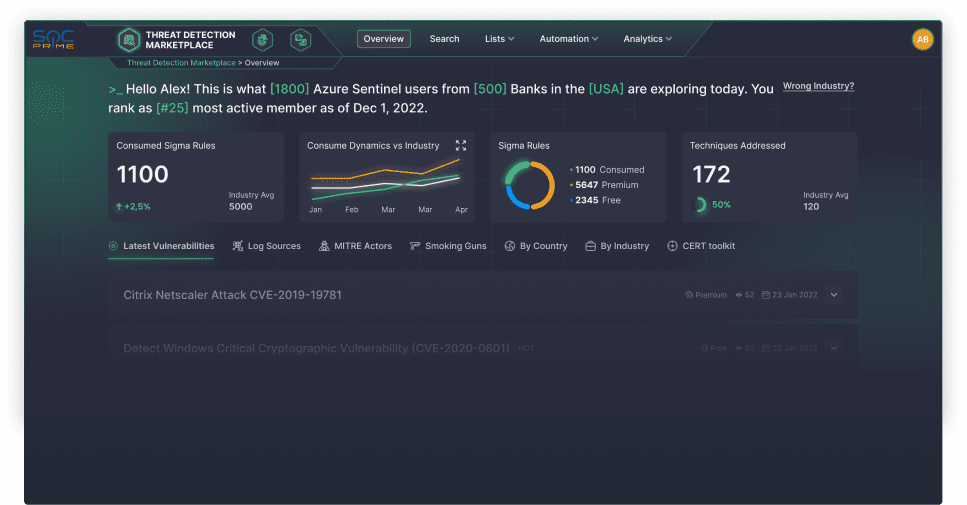
Search for new detection ideas for any threats and TTPs.
Cut through the noise with tailored intelligence.
Centrally manage content and deploy it at scale.
Store all your detection code in a secure environment.
Threat Detection Marketplace is your home where cybersecurity begins.

Reduce Risk
24-hour
Access to the newly released detection code against emerging threats
Optimize SOC Capacity
5 years
Saved of the Detection Engineering backlog
Improve Detection Quality
50%
Less false-positive rate with verified alerts
Boost Detection Velocity
200%
Increase in threat investigation for streamlined detection operations
At the Heart of
Threat Detection
Access the global feed of security news, tailored threat intelligence, and the world’s largest repository of Sigma rules continuously enriched with new detection ideas.
11,000+
Sigma rules to describe any TTPs
28
SIEM, EDR, XDR & Data lake solutions
300,000+
Detections for cloud and on-prem tools
Empower Detection
Customize Content, Optimize Resources
With an ultimate solution that can do it all, you can speed up detection capabilities and free up your security team tons of effort. Find emerging threats and detect cyber attacks faster than ever, accelerate threat investigation, or consolidate and manage all your detection code in an automated fashion from a single place.
Threat Intel & Detection Rules Search Engine
Search for the latest ready-to-deploy behavioral detection algorithms and explore relevant context on any cyber attack or threat, including zero-days, CTI and MITRE ATT&CK references, and Red Team tooling.
Rule Feed on the Latest TTPs
Browse through the world’s largest rule feed on the latest TTPs used by adversaries in the wild, as well as proactive methods not yet linked to cyber attacks. Filter rules to get the most relevant to your industry and geography.
Central Content Management UI for Cloud-Native SIEMs
Automate detection content deployment and management. Arrange detections in curated lists and push customized algorithms directly into your cloud SIEM. Centrally manage content deployed into multiple platforms and track the latest changes.
Custom Repo for Detection-as-Code Projects
Create your custom repositories for Detection-as-Code projects smartly linked to ATT&CK. Save and manage any rules and queries supported by the SOC Prime Platform in a separate encrypted storage to boost the use case management lifecycle.
Drive Collaboration
Backed by collective industry expertise, Threat Detection Marketplace curates free and Premium content feeds continuously enriched and updated to give any security team in the world a significant advantage in their fight against adversaries.
40,000+
SOC Analysts, Threat Hunters & Detection Engineers sharing feedback on detection code
600+
Threat researchers contributing their work as code to help you find current and emerging threats
400
New behavior-based detection algorithms released each month addressing critical threats
Trusted by the Best
More than 9,000 enterprises, including 42% of Fortune 100, 21% of Forbes Global 2000, 90+ public sector institutions, and 300+ MSSP and MDR providers rely on SOC Prime as a trusted partner.
Start Now to Secure Your Tomorrow
Safeguard your organization with the best-in-class technology and professional support. Join the world’s first platform for collective cyber defense. Let’s build a secure tomorrow, together.