Advanced Threat Detection for Enterprise Security
Accelerate your threat detection strategy with a curated feed of behavior rules for emerging
and persistent threats. Cut through the noise with tailored intelligence.
Centrally manage content and deploy it at scale. Store all your Detection as Code in a secure environment.
CONNECTING

45,000+
Users
600+
Threat researchers
9,000+
Organizations
TRUSTED BY

42%
Fortune 100
30%
Global 500
21%
Global 2000




All-In-One Threat Detection Companion
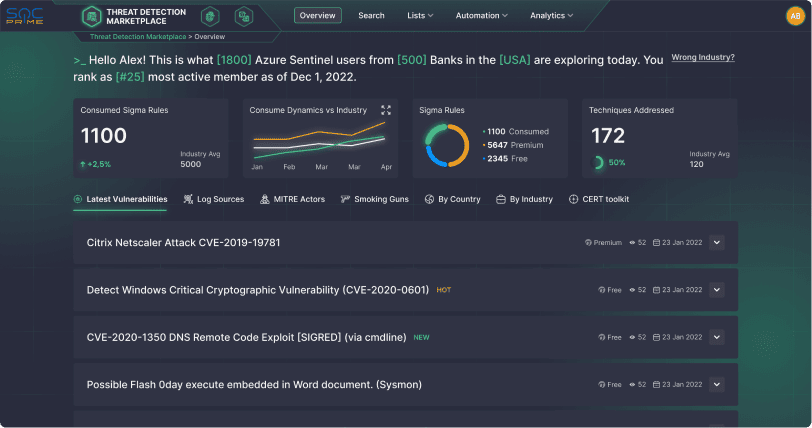
Identify Cyber Threats Before They Escalate
Stop bogging down your team by creating detection content from scratch
- Address existing gaps and obtain bullet-proof detection coverage by relying on ready-to-deploy and easily customizable rules & queries most relevant to your industry, geography, and threat profile.
- Proactively mitigate risks with access to curated detection content against emerging threats available in under 24 hours after their discovery.
- Code faster and smarter to build custom use cases and cover organization-specific log sources with reusable code templates based on over thousands of detection ideas.
24-Hour
SLA for detection content against emerging threats
DIRECTV Latin America relies on SOC Prime’s follow-the-sun detection engineering
operations that ensure round-the-clock protection and proactive defense,
leaving no chance for emerging threats, critical exploits, or adversary TTPs
to go undetected.
SOC Prime’s solution includes a comprehensive library of behavior-based Sigma
rules, enabling the delivery of curated detections 3X faster for any of the
company’s end-customers.
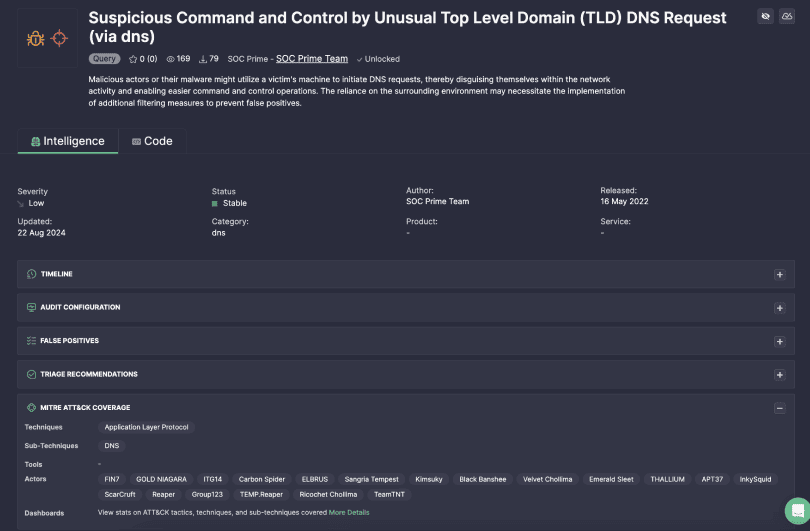
Adopt Out-the-Box Threat Intelligence
Stop struggling to prioritize threat intel feeds to enable data-driven decisions
- Keep up with the latest TTPs used by adversaries in the wild, as well as proactive methods not yet linked to cyber attacks. Prioritize detection content following MITRE ATT&CK, CERT recommendations, per industry usage, or per data feed.
- Explore relevant context linked to 13K+ Sigma rules addressing any cyber attack or threat, including zero-days, CTI and MITRE ATT&CK references, or Red Team tooling to facilitate operationalizing your threat intelligence.
50%
Faster MTTD & MTTR to ensure no attack goes undetected
Instant access to CTI integrated with Sigma rules streamlines the in-house
engineering team’s daily security operations and simplifies the time-intensive
process of gathering intelligence from various sources.
Leveraging the MITRE ATT&CK content visualization functionality in the SOC Prime
Platform has helped 7Layers to streamline the search for detection and hunting
content by particular TTPs matching the end-customers’ threat profiles,
address prioritization hurdles, and fill the gaps in threat detection coverage.
Leveraging SOC Prime Platform as a core source of threat intelligence enables
SOC and CTI analysts to save at least 60 hours each month on threat research
instead of drowning in overwhelming data.
Improve Detection Quality
Stop missing threats due to gaps in detection logic
- Equip your team with the world’s largest collection of threat detection rules for your SIEM, seamlessly configure them, and automatically deploy to generate low-noise, high-value alerts.
- Act faster than attackers with verified behavior-based hunting queries for streamlined threat research while correlating the outcomes with ATT&CK and actionable CTI.
- Harness MITRE ATT&CK and every detection ever created as your dictionary for rapidly developing new code with flawless quality. Seamlessly translate verified rules to any SIEM, EDR, or Data Lake format you need.

50%
Reduced false positive rate
Neurosoft has significantly improved MTTD and MTTR and cut down the
false positive rate by up to 50% over the first 6 months of using the Platform.
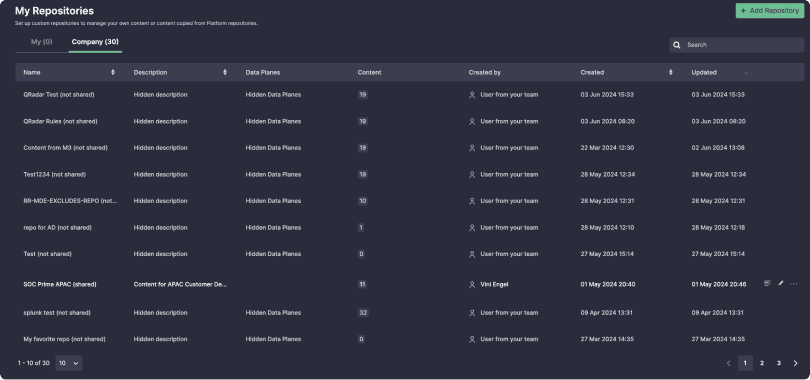
Automate Content Management Workflows
Stop burdening your team with manual content management and deployment tasks
- Automate detection logic streaming directly into your SIEM instance. Centrally manage content deployed into multiple platforms and track the latest changes to the content in production. Download content translations via API to on-prem and cloud environments.
- Save and manage detection code in a separate encrypted storage hosted at SOC 2 Type II AWS private segment with 99,5% uptime SLA, no IP transfer, and full compliance with content Privacy Assurance.
5 Years
Saved on the Detection Engineering backlog
With SOC Prime, LTIMindtree’s clients can continuously stream up-to-date
detection algorithms directly into their environment.

Gartner Peer Insights Reviews
Explore Our Use Cases
Maximize
Threat Detection Performance
Drive the best ROI of threat detection while adopting proactive defense against imminent and persistent threats. Equip your security team with the complete product suite for AI-powered Detection Engineering, Automated Threat Hunting and Detection Stack Validation to smartly resolve your existing challenges with a single end-to-end workflow.














