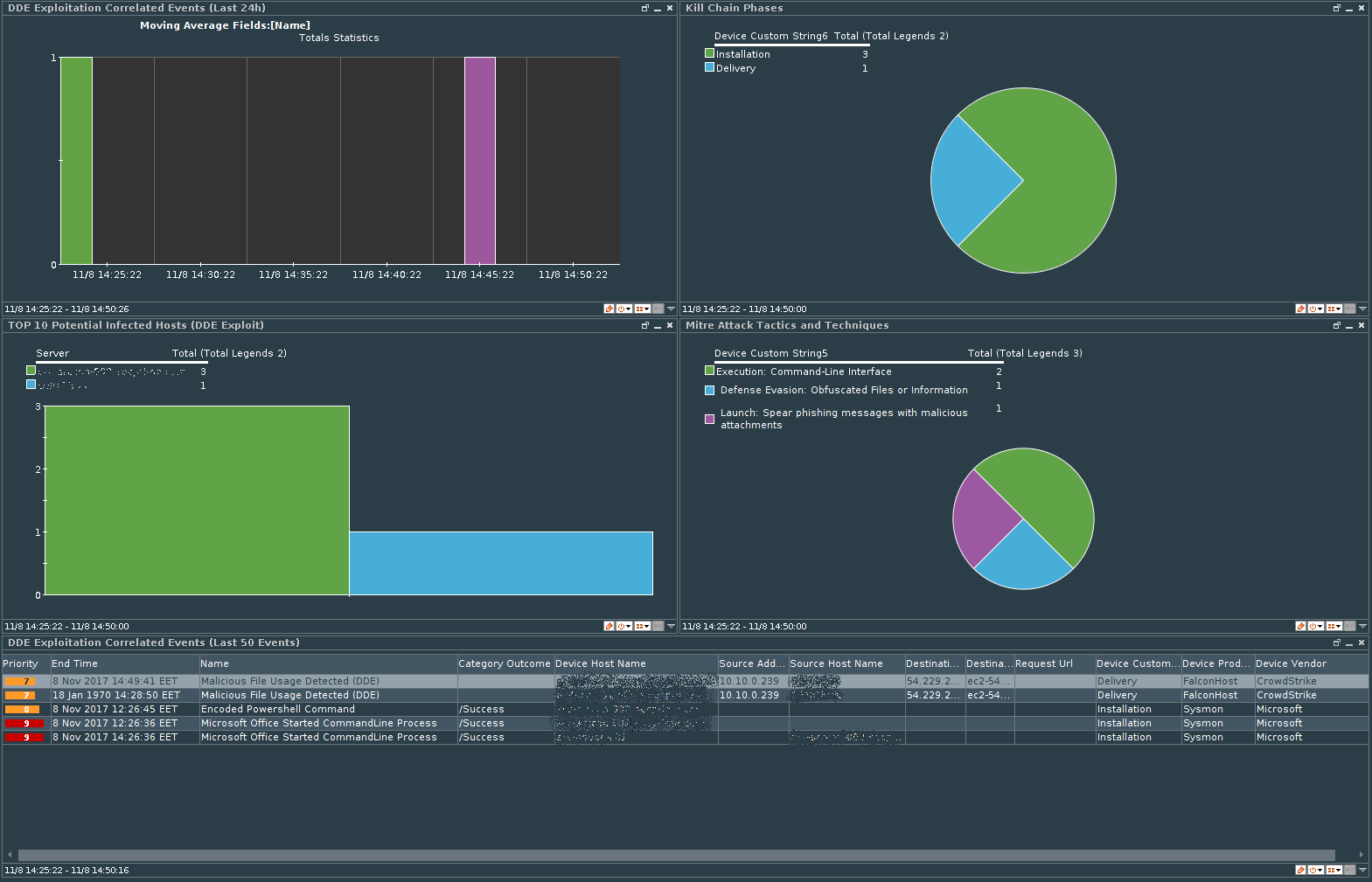
DDE Exploitation detector is turn-key SIEM content to automatically uncover abuse of Microsoft Office Dynamic Data Exchange for delivering malicious payloads. As reported by multiple security vendors exploiting DDE vulnerability (or feature?) became popular in October 2017. Anything in Microsoft Office can be exploited including Word, Excel, PowerPoint, OneNote and even Outlook using calendar invites. Multiple actors and tools use this attack technique including Fancy Bear / APT 28, Fin7, Necurs Botnet, Locky, Hancitor malware and others. By studying the attacks, we can use MITRE ATT&CK to classify DDE exploit used in Launch tactic and Spear phishing messages with malicious attachments. Once files are opened a cmd.exe or powershell.exe is launched to initiate download of malicious code to victim’s computer. Script contents are encoded with Base64.
Use case contains 96 IOCs including IP, Port, URL, File hashes and File names. Dashboard is included for both individual analyst and SOC usage. SOC channel is also included flagging events with different priorities for events of interest. All events are tagged according to Cyber Kill Chain and MITRE ATT&CK attributing to 4 tactics and 6 techniques. This SIEM content works based on Firewall and Proxy events, Sysmon and CrowdStrike Falcon EDR log data.
As DDE is considered a legitimate feature of Microsoft Office suite by default, it will bypass most antivirus products, sometimes even without warning. As of November 8, 2017, it is unclear if Microsoft plans to mitigate this attack vector or remove such functionality.
One of the common mitigation recommendations is to disable "update automatic links at open" option in Microsoft office suite. An example fix for Microsoft Word that you can apply by yourself: Open Word → Select File → Options → Advanced and scroll down to General and then uncheck "Update Automatic links at Open." These settings are individual for each Office program, so a standard security baseline also applies – do not open attachments from someone you did not expect, never click on the links in such documents and block outgoing communications from Microsoft Office applications to all resources except the ones you trust.
You can also update registry with following keys from Null Byte / wdormann: https://gist.github.com/wdormann/732bb88d9b5dd5a66c9f1e1498f31a1b
More useful links:
https://malwarenailed.blogspot.ae/2017/10/dde-exploitation-detection.html
https://thehackernews.com/2017/10/ms-office-dde-malware-exploit.html
Hiding DDE exploits: https://null-byte.wonderhowto.com/how-to/hide-dde-based-attacks-ms-word-0180784/
Avoiding security warnings: https://null-byte.wonderhowto.com/how-to/execute-code-microsoft-word-document-without-security-warnings-0180495/
Calendar invites with DDE: https://twitter.com/dirty_tizzle/status/921454997262536705