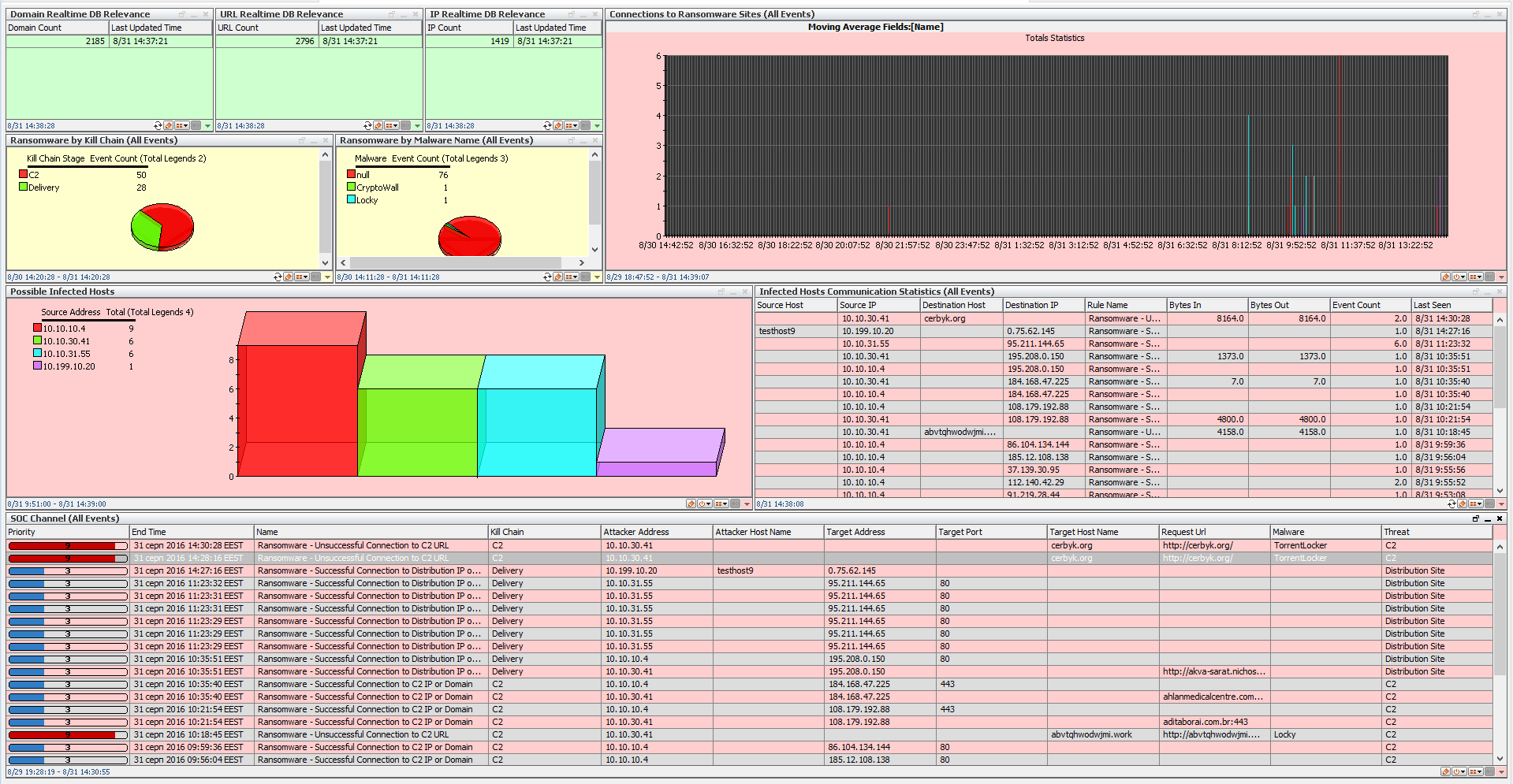
Ransomware Hunter natively integrates with SIEM systems and leverages stastical profiling and behavioral analysis methods, OSINT feeds including Ransomware Tracker by Abuse.ch and Detect Tor feed as well as strictly defined correlation rules. This enables organizations to spot and stop any Ransomware as early as possible. Due to adversaries continuously bypassing traditional defense systems in both wide-spectre and targeted attacks (APT), accurate and timely detection followed by Incident Response can completely prevent any threat and damage posed by Ransomware. Ransomware Hunter provides detection and automatic alerting capabilities at Reconnaissance, Delivery, Exploitation, Installation, Command and Control (C2) and Action on Objectives phases, thus covering full threat Life-cycle according to Cyber Kill Chain methodology.