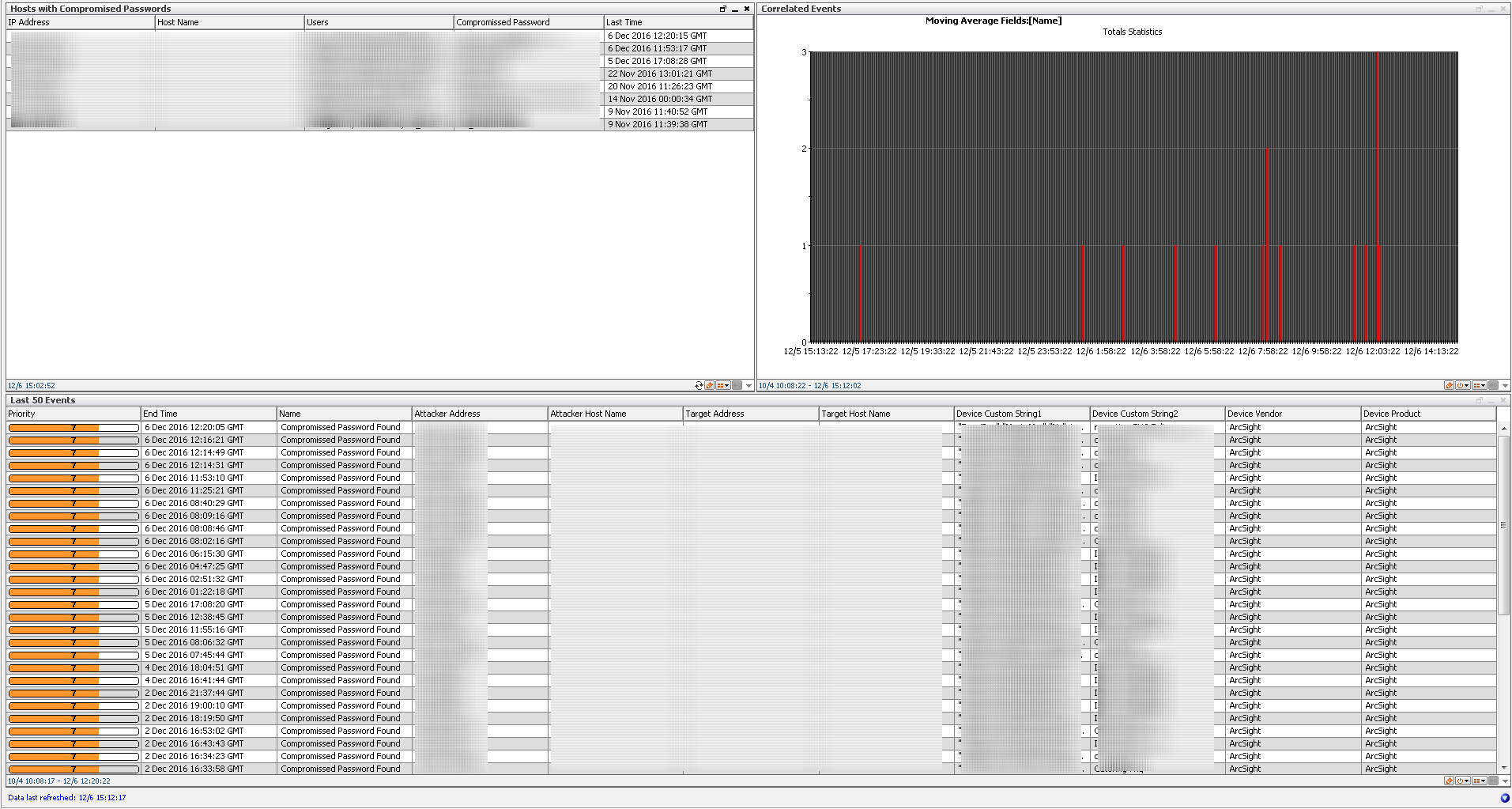
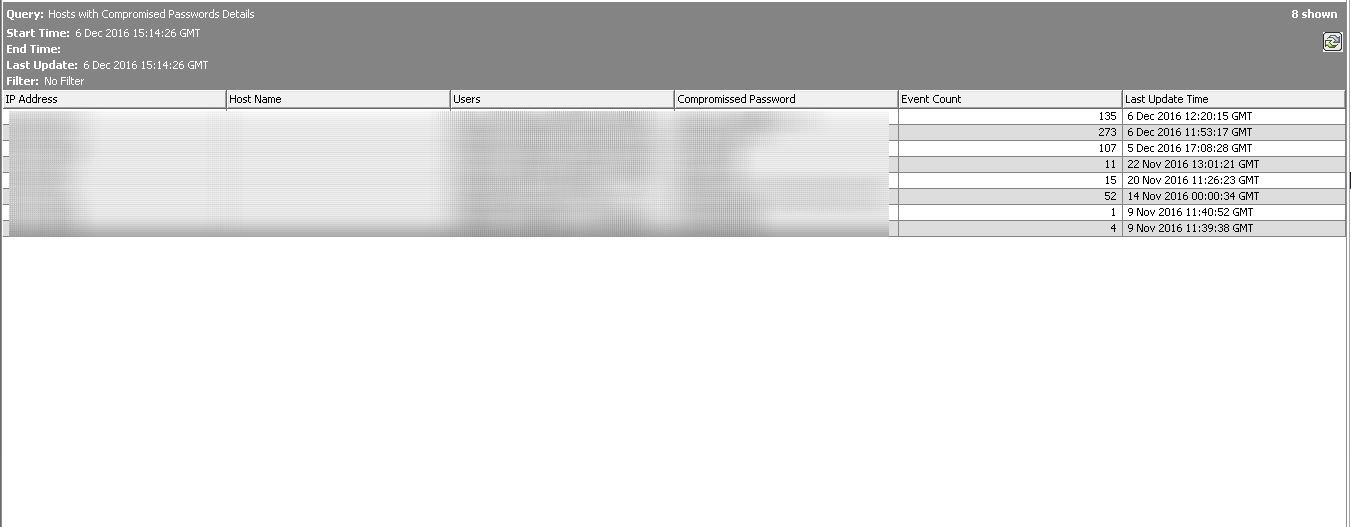
A framework for monitoring password security that allows to find compromised passwords by checking Microsoft Windows authentication logs for usernames that contain passwords. Use case includes a set of rules to perform real-time regex search for passwords in usernames containing numbers, special characters etc. As a result, we form list of hostnames and affected users that are likely compromised – someone could see password on the screen when user mistyped it, also authentication failure is logged to Windows Event Log that is not encrypted. Thus, all accounts discovered by the use case must be investigated further. Dashboard displays list of hosts with compromised passwords, spikes of such authentication events and last 50 events. Initial version monitors only Microsoft Windows events, next version is already in R&D to include any authentication logs.