Perhaps you have already heard of the 1998 vulnerability in RSA originally discovered by Daniel Bleichenbacher. It has now resurfaced as Return of Bleichenbacher's Oracle Threat aka ROBOT attack. Long story short the vulnerability allows attackers to passively record traffic and decrypt data without having a private key.
The most comprehensive guide on vulnerability, risk and impact is published by Hanno Böck, Juraj Somorovsky (Hackmanit GmbH, Ruhr-Universität Bochum), Craig Young (Tripwire VERT) at hXXps://robotattack[dot]org
Full paper published at the Cryptology ePrint Archive
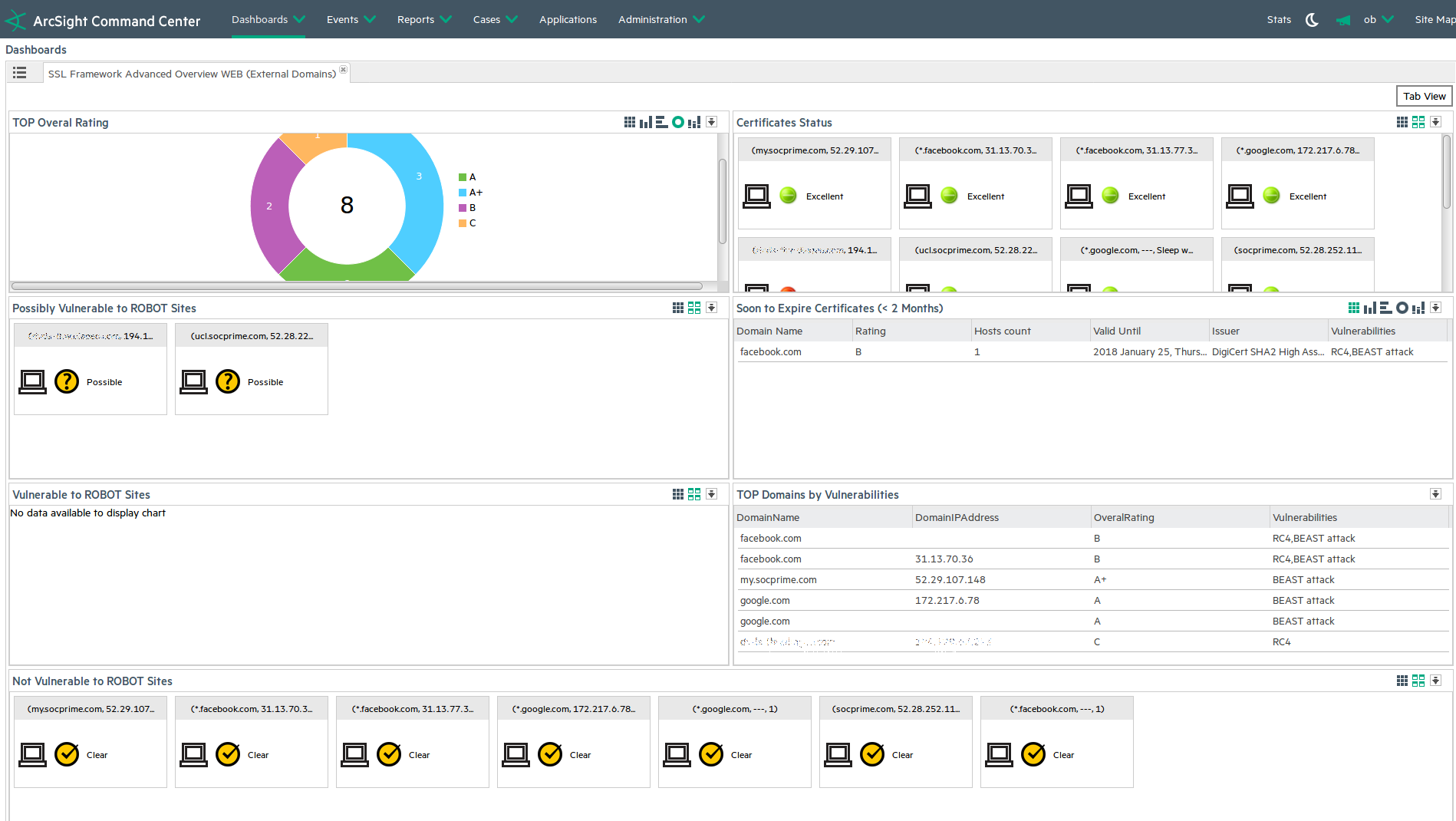
SSL Framework advanced is a turn-key SIEM content that uses Qualys SSLLabs, open-source scripts and QualysGuard Vulnerability Management data on SSL/TLS certificates to continuously track, provide a holistic view and automatic alerting on any vulnerabilities in TLS digital certificates and their proper implementation. The advanced version includes:
- Python connector to SSLLabs API
- ROBOT-attack detection script by https://github.com/robotattackorg/robot-detect/blob/master/robot-detect
- hXXps://testssl.sh
- HiTechBridge API connector is planned for Q1 2018
SSL Framework automates the monitoring and alerting process on:
Self-signed, Revoked and Wildcard certificates;
Detection of common vulnerabilities that can lead to attacks from Heartbleed to DROWN and ROBOT attack.
All alerts and holistic certificate view is displayed in SIEM dashboard for ArcSight, QRadar or Splunk.
REMEDIATION & MITIGATION
The most complete remediation is to disable RSA encryption-based key exchange modes where possible. This guarantees protection against known and unknown vulnerabilities with a minimal impact on HTTPS client compatibility.
Software vendors have already released patches and configuration guides. A tracker is published at hXXps://robotattack[dot]org
Table with references as of Wednesday, December 13, 2017:
|
F5 |
||
|
Citrix |
||
|
Radware |
Security Advisory: Adaptive chosen-ciphertext attack vulnerability |
|
|
Cisco ACE |
||
|
Bouncy Castle |
Fix in 1.59 beta 9, Patch / Commit |
|
|
Erlang |
||
|
WolfSSL |
||
|
MatrixSSL |
||
|
Java / JSSE |