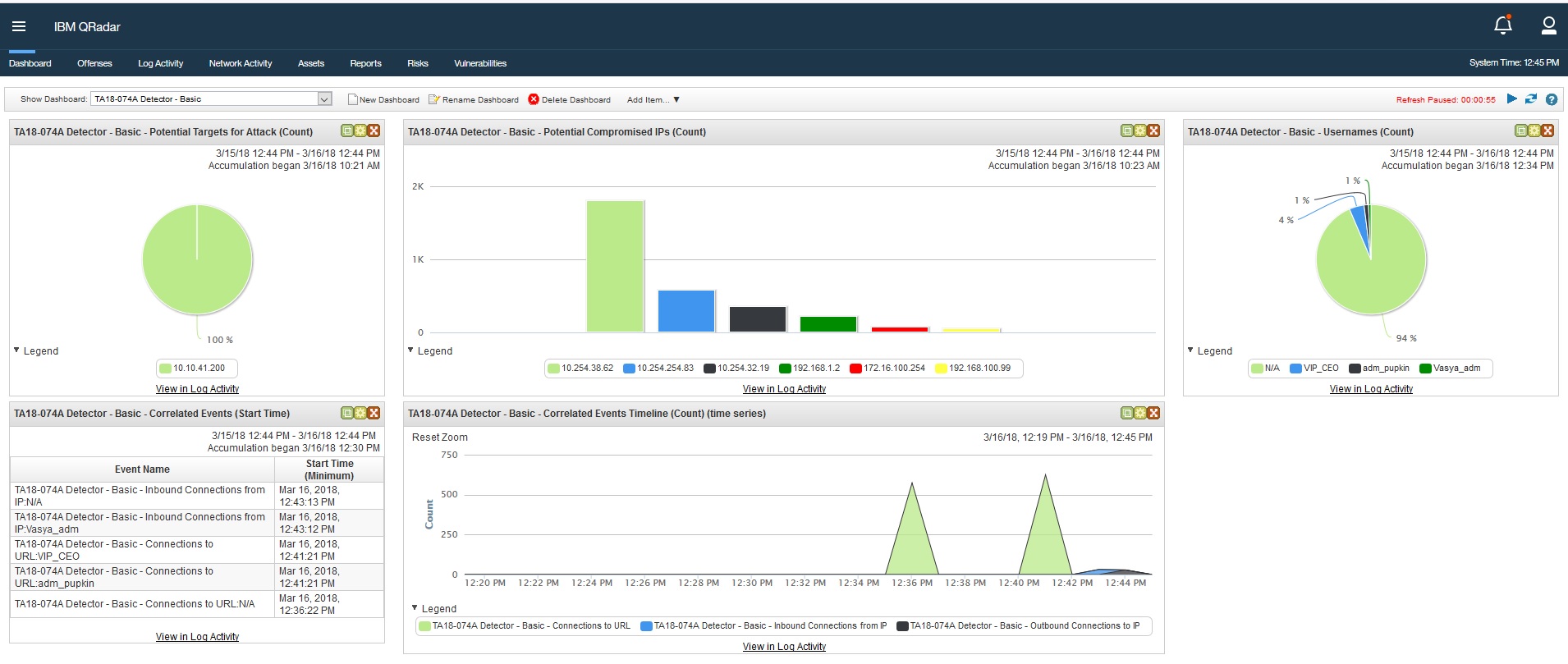
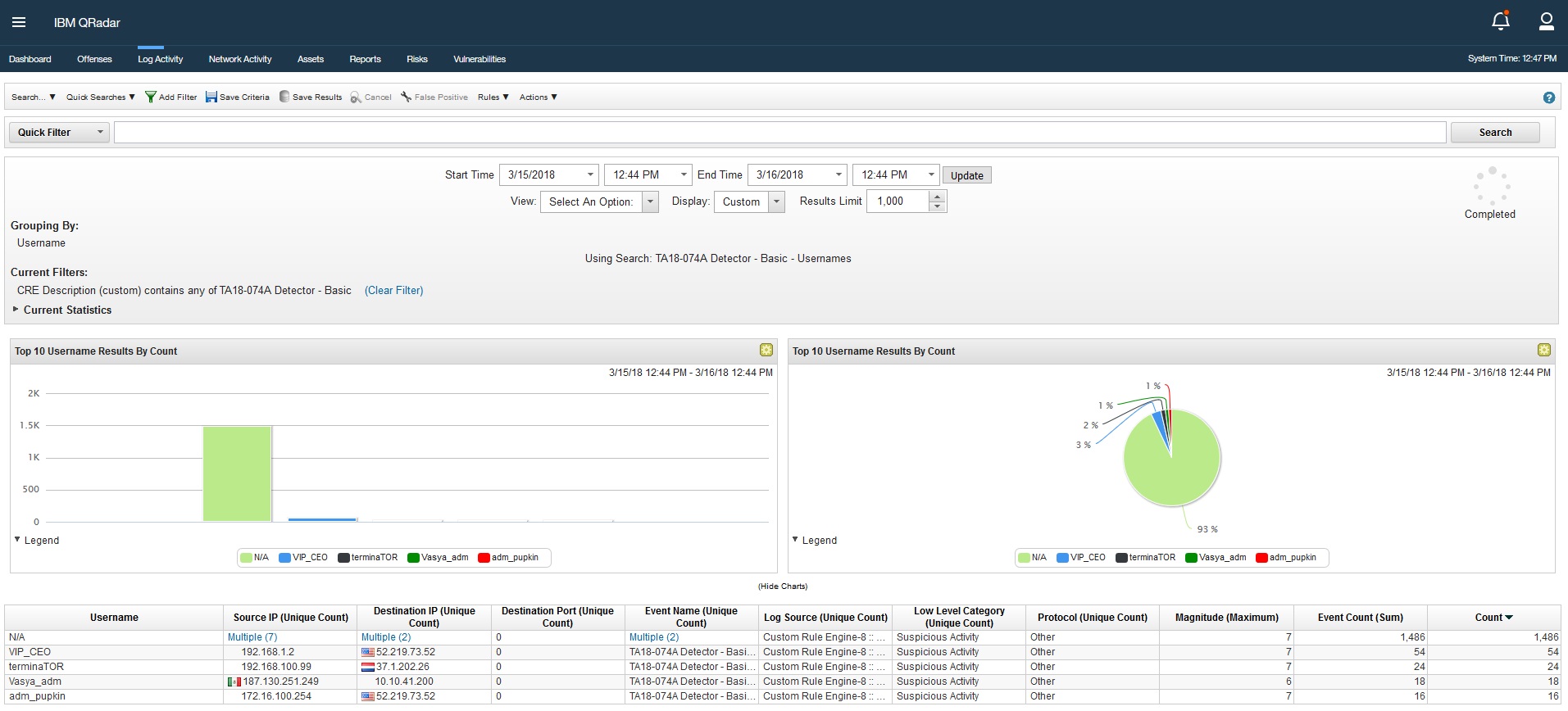
This is a turn-key content package issued within same day of TA18-074A US-CERT alert https://www.us-cert.gov/ncas/alerts/TA18-074A to help detect compromised assets and activity of Dragonfly 2.0 / Berserk Bear / Energetic Bear. Contains 128 IOCs including URL, IP, MD5, SHA-1 and SHA-256 hashes. IOCs are populated to reference sets for real-time monitoring. 82.5% of IOCs are gathered from US-CERT alert and 17.5% from Anomali ThreatStream Community, all IOCs are TLP:WHITE. SOC Dashboard is included along with Cyber Kill Chain tagging and event channel. In the archive we also include IOC search queries for QRadar for historical analysis. It is recommended to run these searches for the longest time period possible.
We excluded the following 4 hashes from the case as they are not present in TA18-074A, however they were present in TA-17-293A. You can add them to active list if you want to monitor for them too but watch out for false positives.
*A7F7A0F74C8B48F1699858B3B6C11EDA
*AEEE996FD3484F28E5CD85FE26B6BDCD
*E29D1F5D79CD906F75C88177C7F6168E
*FCC093A79FAE9B92E69C99BB28F9AE12939E4E1327A371EEAC9207E346ECCDB4