

SIGMA - one common language for cybersecurity
-
2016
-
December 24

Invention of Sigma
Florian Roth and Thomas Patzke made the first-ever public commit to the GitHub repo devoted to Sigma, which initiated the birth of “a common language for cybersecurity.”
-
December 24
-
2017
-
February 14

Elasticsearch Query Backend
Elasticsearch Query backend for Sigma v.1 was committed by Thomas Patzke to the dedicated open source GitHub repository.
-
September 22

Elastic Stack X-Pack Watcher Backend
Elastic Stack X-Pack Watcher backend for Sigma v.1 was shared by Devin Ferguson and Thomas Patzke via GitHub.
-
March 3

Splunk Query Backend
Splunk Query support was added to Sigma and shared by Thomas Patzke with the project followers via GitHub.
-
March 18

LogPoint Backend
LogPoint backend for Sigma developed by Ben de Haan was uploaded to the community GitHub repository by Thomas Patzke.
-
March 26

MISP Support
Malware Information Sharing Platform (MISP) added support for the Sigma language with the release of MISP version 2.4.70.
-
May 3

ArcSight, QRadar, and Qualys Backends
SOC Prime founders – Andrii Bezverkhyi, Oleksandr Bredikhin, and Ruslan Mikhalov – joined the Sigma community and started collaboration to add more backends to the Sigma standard, initially headlining ArcSight, QRadar, and Qualys backend development.
-
June 28

First-Ever MITRE ATT&CK® Tagging
Sigma rule for NotPetya Ransomware Activity detection was developed and shared with the community by Florian Roth and Tom Ueltschi. Simultaneously, the SOC Prime Team helped the victims of the NotPetya attack on-site and remotely using Sigma rules alongside its own SIEM-native content. The detections were tagged with MITRE ATT&CK® and Lockheed Martin Cyber Kill Chain (LMCKC) to extract TTP-based behaviors for threat actor attribution. As a result, 83% of TTP-based attributions to the Sandworm Team were confirmed, fully reported, and shared publicly within 5 days. The investigation of the NotPetya attack was a prominent event for spreading a word about Sigma. For the first time in history, Sigma rules tagged with MITRE ATT&CK were successfully used for threat hunting.
-
August 29

Initial ATT&CK-Based Correlation
The first-ever MITRE ATT&CK-based correlation was made by SOC Prime leveraging Sigma rules and Elastic Stack X-Pack Watcher. This preceded the release of the Elastic Stack detection rules and SIEM correlation capabilities by 30 months.
-
February 14
-
2018
-
January 10

Pioneer Commercial Support
The world’s first commercial support for Sigma rules was launched by SOC Prime powered by the company’s SaaS platform, Threat Detection Marketplace. Initially, it was provided for the original Elasticsearch and Elastic Stack X-Pack Watcher, Splunk Query, as well as newly-developed backends by SOC Prime for ArcSight, QRadar, and Qualys.
-
April 2
Sigma UI Release
Sigma UI application for the Elastic Stack was released by SOC Prime via GitHub. The application supported tagging Sigma rules with MITRE ATT&CK, thus marking the first-ever public open-source interconnection between Sigma and the ATT&CK framework.
-
May 24

Sigma Intro at First EU ATT&CK Workshop
The 1st EU ATT&CK Community Workshop took place at the Computer Incident Response Center Luxembourg (CIRCL). By invitation of Freddy Dezeure, SOC Prime’s Founder and CEO, Andrii Bezverkhyi, presented a session to introduce Sigma to the MITRE community and showcase tools and capabilities for tagging Sigma rules against the MITRE ATT&CK matrix. CIRCL members, MISP founders, MITRE representatives alongside the leading European SOCs and CERTs voted for approving the course of tagging Sigma with MITRE ATT&CK. This initiative has become a golden standard that currently ensures extensive visibility of organization-specific threats worldwide.
-
May 25

Microsoft Defender ATP Backend
The first version of Microsoft Defender ATP backend for Sigma was added to the community GitHub repository by Thomas Patzke.
-
June 28
Sigma Scanning for THOR
Florian Roth, CTO of Nextron Systems and the author of THOR APT Scanner, added support for Sigma rules checking on endpoints to his incident response scanning tool.
-
July 11

Public GitHub Repo for ArcSight, Qualys, and Graylog
ArcSight and Qualys backends developed by SOC Prime, as well as the Graylog backend, developed by Paul Duot, were merged for Sigma and publicly shared via GitHub repository.
-
July 22

QRadar Backend Shared via GitHub
QRadar backend for Sigma was shared via the community GitHub repository by SOC Prime.
-
September 6
Uncoder.IO Release
SOC Prime released Uncoder.IO — a free and private online translation engine powering one-click conversions from Sigma rules to SIEM saved searches, filters, queries, API requests, and correlations.
-
October 17
Sigma Overview at 13th Hack.lu
The 13th Hack.lu conference took place hosted by Thomas Patzke, who introduced the basics of how to create Sigma rules and use them to hunt for threats in logs.
-
October 31

RSA NetWitness Backend
RSA NetWitness backend for Sigma was committed to the GitHub Sigma repository by John Tuckner.
-
December 10

Sumo Logic Backend
Sumo Logic backend for Sigma, developed by Florian Roth and Thomas Patzke, was publicly shared via the GitHub Sigma repo.
-
January 10
-
2019
-
February 13

Sigma Highlights at First SANS Webcast
First-ever SANS Webcast devoted to Sigma went live. The “MITRE ATT&CK and Sigma Alerting” session provided insights into the Sigma Alert project and the practice of creating alert rules against the MITRE ATT&CK framework items to discover attacks.
-
March 4

Microsoft Azure Sentinel Backend
Microsoft Azure Sentinel backend for Sigma v.1 was publicly shared with the community via GitHub by John Tuckner.
-
May 9

Threat Bounty Announced at 3rd EU ATT&CK Workshop
The 3rd EU ATT&CK Community Workshop took place at EUROCONTROL, Brussels. At this major international event, SOC Prime Founder, Andrii Bezverkhyi, held a session to announce the launch of SOC Prime’s Threat Bounty Program that rewarded individual researchers for the development of threat hunting algorithms linked to Sigma. Also, the session summarized the one-year practice of tagging Sigma against the MITRE ATT&CK framework.
-
July

Compliance-Based Sigma
SOC Prime Team developed the first Sigma rules for Compliance linking queries to the industry Compliance standards, such as GDPR, PCI DSS, ISO27001, and CIS CSC.
-
October 3

Sigma First-Ever Mention by Gartner
Gartner mentioned Sigma for the first time in its Cool Vendors in Security and Risk Management, 2H19 research. In this document, SOC Prime was recognized as a Cool Vendor with its Threat Detection Marketplace platform providing detection content using Sigma, “a generic and open SIEM signature format, which is becoming a common method to develop content that can be used across different solutions.”
-
October 25

Insights into Sigma & ATT&CK Mapping for Cloud
4th EU ATT&CK Community Workshop & Hack.lu took place in Luxembourg. At this event, SOC Prime’s Founder, Andrii Bezverkhyi, presented how to use Sigma for cloud threat detection (AWS, Office365, Azure GCP, G-Suite) and introduced initial mappings to ATT&CK for the cloud.
-
December 1
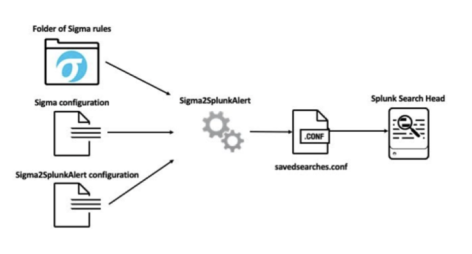
Sigma2SplunkAlert GitHub Repo Launch
To streamline Sigma rules deployment into Splunk, Patrick Bareiss launched a dedicated Sigma2SplunkAlert GitHub repository. It allows converting Sigma rules to Splunk Alert configurations leveraging the power of Jinja2 templating to generate a Splunk savedsearches.conf.
-
December 30

MISA Membership
Microsoft Azure Sentinel backend for Sigma received the first active contribution from SOC Prime as part of its membership in the Microsoft Intelligence Security Association (MISA). After joining MISA, SOC Prime became one of the most active backend contributors for Azure Sentinel together with Thomas Patzke.
-
February 13
-
2020
-
February 24

Carbon Black Query Backend
Carbon Black Query backend for Sigma developed by SOC Prime was added to the community GitHub repository.
-
February 24-28

RSAC 2020: Microsoft and SOC Prime’s Collaboration
By invitation from Microsoft, Andrii Bezverkhyi, Founder and CEO at SOC Prime, and Ofer Shezaf, Principal Product Manager at Microsoft, shared the stage at RSAC 2020 to present the joint project on enabling Sigma support for Microsoft Azure Sentinel Queries & Rules and dedicated streaming capabilities for Microsoft API.
-
April 7
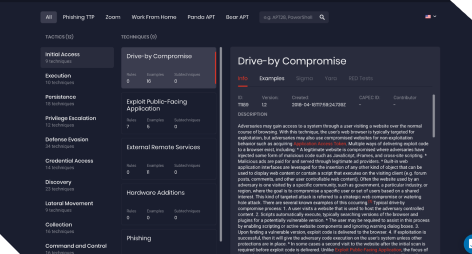
MITRE ATT&CK Map Release
SOC Prime launched attack.socprime.com — a first-ever free public project that supported MITRE ATT&CK v.7 beta (including sub-techniques), introduced the horizontal view of MITRE ATT&CK matrix, and linked it with Sigma rules.
-
May 8

Humio Query Backend
Humio Query support was added to Sigma by SOC Prime and shared with the community via the GitHub Sigma repo. That day, SOC Prime also shared its version of the enhanced Splunk backend for Sigma to expand it with the support for CrowdStrike Query.
-
May 14
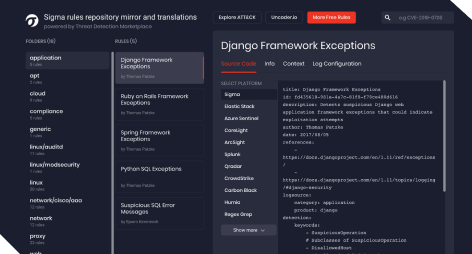
Sigma Rules Repository Mirror
SOC Prime released the Sigma rules repository mirror powered by Threat Detection Marketplace and synced it with the open source GitHub repository managed by Florian Roth to ensure extensive availability of behavior-based Sigma rules for the cybersecurity community.
-
May 18-19

Sigma Insights at 5th EU ATT&CK Workshop
The 5th EU ATT&CK Community Workshop took place at the European Commission, Brussels. At this major international event, Andrii Bezverkhyi, Founder and CEO at SOC Prime, held a session to dive deep into the practical and scientific approaches to MITRE ATT&CK, introduced the horizontal view of the MITRE ATT&CK matrix for more convenience, and shared insights on using Sigma rules to prioritize the order of ATT&CK techniques.
-
August 18

Sysmon Backend
Sysmon backend able to generate relevant configs for Sigma was developed by SOC Prime and publicly shared with the community via the GitHub repository.
-
November 19

FireEye Backend
FireEye backend for Sigma was added to the community GitHub repository by Alek Rollyson.
-
February 24
-
2021
-
January 27

SentinelOne Backend
SentinelOne backend for Sigma was developed by SOC Prime and added to Threat Detection Marketplace to provide exclusive commercial support for it.
-
March 12

Chronicle Security Backend
Google Chronicle Security backend for Sigma was publicly shared with the community and uploaded to the dedicated GitHub repository by SOC Prime. Additionally, support for Sigma to YARA-L conversions was introduced to Uncoder.IO to enrich both cybersecurity standards with compatible detection content.
-
April 14

SOC Prime’s Innovation Report 2020
SOC Prime published its Detection as Code Innovation Report 2020 to summarize the collaborative efforts of the SOC Prime Team, Threat Bounty Program content contributors, and the worldwide community in fighting critical threats of 2020 by means of Sigma rules and open-source Detection as Code content.
-
June 1-2

Sigma Customization at 7th EU ATT&CK Workshop
At the 7th EU MITRE ATT&CK® Community Workshop , SOC Prime’s Founder and CEO, Andrii Bezverkhyi, presented a session about best practices in Sigma customizations, summarizing how the community-driven approach can contribute to Sigma establishment as an industry standard.
-
June 16

Securonix Backend
Securonix Team has developed the initial Sigma backend and partnered with SOC Prime to make it available globally. Following the release, the commercial support for this backend was launched via Threat Detection Marketplace.
-
June 25
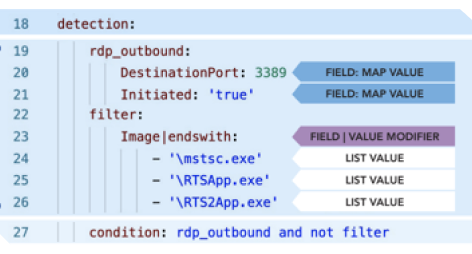
Detection Engineering with Sigma
A detailed cheat sheet describing the basics of detection engineering with Sigma was released by Josh Brower and Chris Sanders.
-
June 29

Sigma Mention in 2021 MQ for SIEM
Sigma was mentioned in the 2021 Gartner, Magic Quadrant for SIEM as a recommendation to improve the capabilities of the standard support for one of the MQ leading SIEM technologies.
-
June 30

Splunk Alert Backend
Splunk Alert backend for Sigma was developed by SOC Prime and the commercial support for it was enabled via SOC Prime’s Threat Detection Marketplace. This backend supports automated content streaming into users’ instances with the help of Continuous Content Management module to streamline the SOC operations.
-
July 13
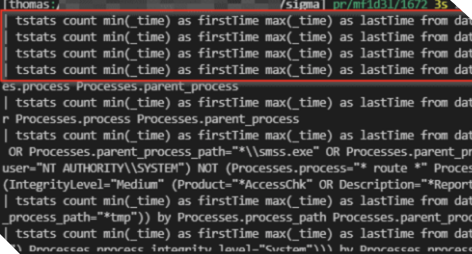
Splunk Data Model for Sigmac
A dedicated backend that supports the Splunk syntax leveraging data model acceleration was developed by mfidel, publicly shared via SigmaHQ GitHub repository, and added to Sigmac tool.
-
July 15

Insights into Sigma Capabilities at 2021 SANS Webcast
SANS Webcasts “How to Level Up Your Threat Detection Practice” with Dr. Anton Chuvakin, Andrii Bezverkhyi, and Matt Bromiley went live. In this session, the speakers delved into scientific approaches on how to use Sigma from the development point of view and discussed correlation capabilities and complexity of Sigma algorithms, considering the trends in security operation approaches worldwide.
-
July 20
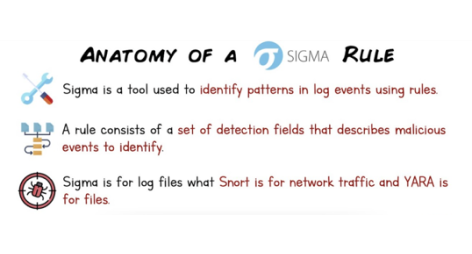
Anatomy of a Sigma Rule
Thomas Roccia released a comprehensive cheat sheet on Sigma rules creation to provide crisp and handy tips for all Sigma project followers.
-
July 30

Sigma Mention in 2021 Gartner’s Research Note
Gartner’s research note “How to Use MITRE ATT&CK to Improve Threat Detection Capabilities” mentioned Sigma detections as “generic rules which integrate with many different SIEM solutions” and enable mapping to the MITRE ATT&CK matrix.
-
September 11
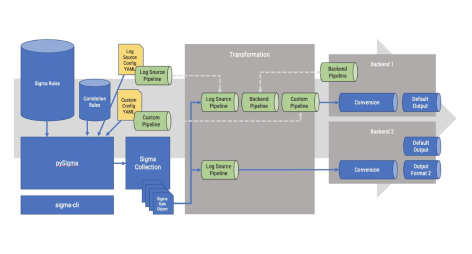
Launch of pySigma GitHub Repository
The pySigma GitHub repo was launched by Thomas Patzke and Florian Roth to provide a Python library for parsing, transformation, and conversion of Sigma rules. The pySigma repo improves the logic of the Sigmac tool and streamlines the conversion process from a Sigma rule into query languages by providing corresponding conversion backends.
-
January 27

GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.