Package for security monitoring of Microsoft Office365 SaaS ready for deployment on Microsoft Sentinel to detect incidents and security violations in the Office365 platform.
Includes 26 threat detections covering 8 Techniques across 6 Tactics according to MITRE ATT&CK Enterprise.
SOC Prime Platform provides integration with Microsoft Sentinel that allows deployment of rules directly from the Platform web console.
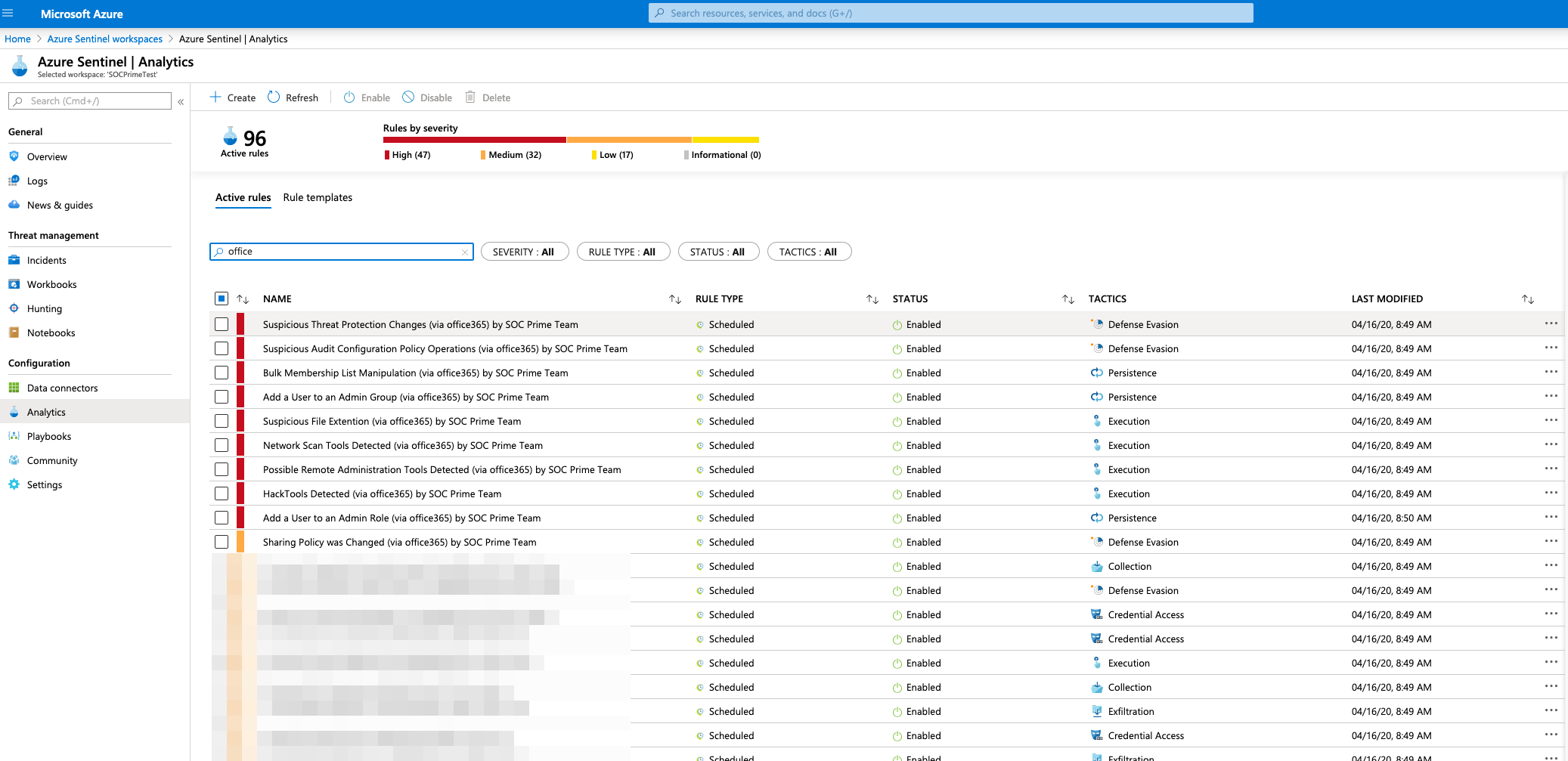
First 10 rules from 26 that are in the Content Pack:
- Suspicious Threat Protection Changes (via office365) by SOC Prime Team
- Suspicious Audit Configuration Policy Operations (via office365) by SOC Prime Team
- Bulk Membership List Manipulation (via office365) by SOC Prime Team
- Add a User to an Admin Group (via office365) by SOC Prime Team
- Suspicious File Extension (via office365) by SOC Prime Team
- Network Scan Tools Detected (via office365) by SOC Prime Team
- Possible Remote Administration Tools Detected (via office365) by SOC Prime Team
- HackTools Detected (via office365) by SOC Prime Team
- Add a User to an Admin Role (via office365) by SOC Prime Team
- Sharing Policy was Changed (via office365) by SOC Prime Team
MITRE ATT&CK tags:
- Execution | T1204
- Valid Accounts | T1078
- Account Manipulation | T1098
- Brute Force | T1110
- Remote File Copy | T1105
- Data Staged | T1074
- Email Collection | T1114
- Automated Exfiltration | T1020
Note: Organizations can access detection content and modules available in the SOC Prime Platform according to their active subscription plan.