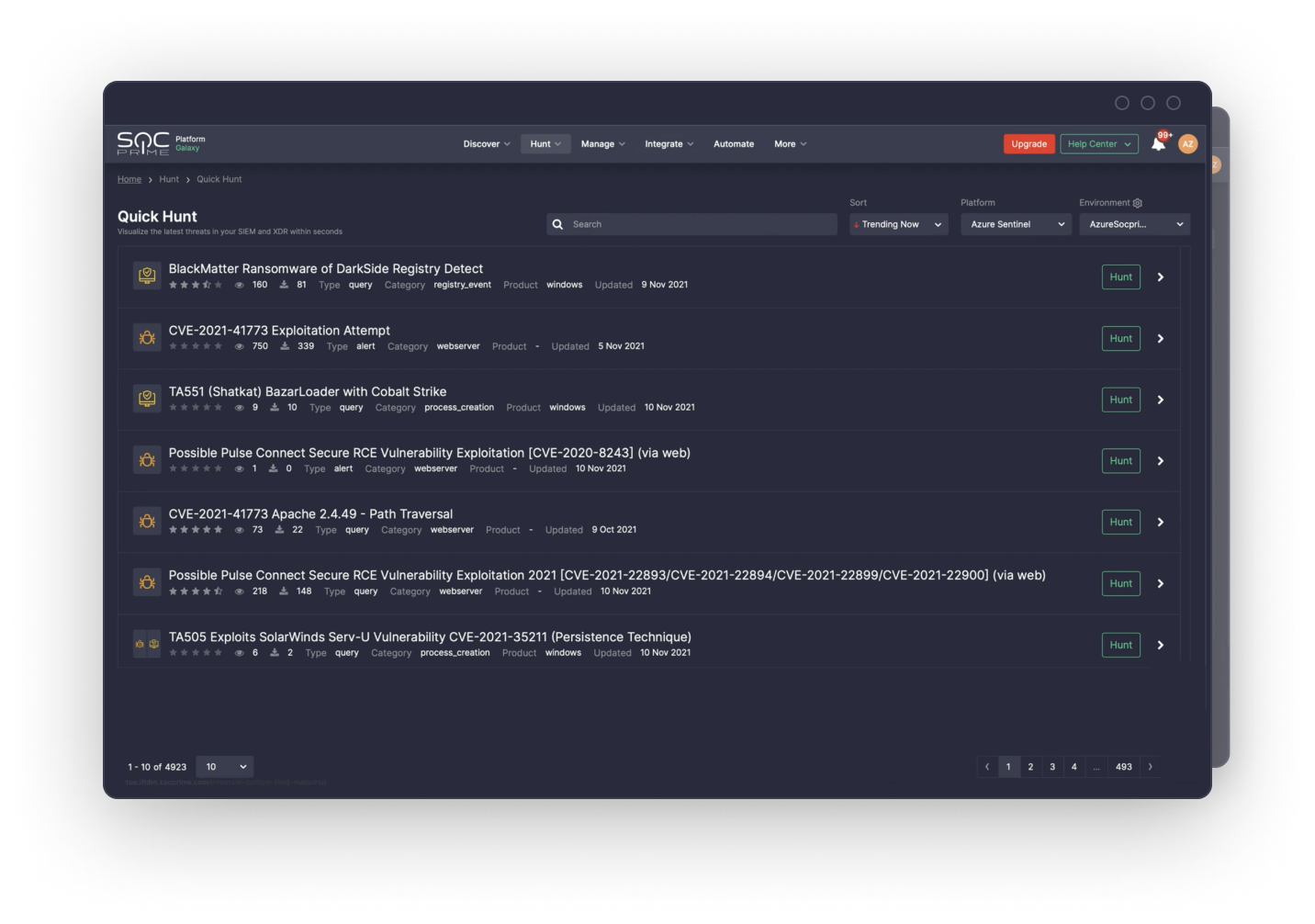
Quick Hunt: Threat Hunting Made Easier with a Power of Community
With Quick Hunt, anybody can become a threat hunter — no matter if you are a seasoned security expert, or it's your first day on the job, searching for the latest threats is easier than ever before.
HUNT NOW WATCH DEMOGet Started in 3 Simple Steps
Threat hunting is a hard skill to master, and talent shortage in the field makes high demands on organizations. Quick Hunt makes it simple by turning a capability into an attribute.
Get informed
Focus on threats most relevant to your organization and the security tool in use. For a more deep dive, explore relevant cyber threat intelligence, media mentions, CVE and MITRE ATT&CK® links.
Hunt in your SIEM or EDR
Single-click to land at your pre-configured Data Plane, get the query pasted into your browser address bar, and view the results of your hunt.
Share feedback
Share your feedback with the community and get one back from your peers across the world to make hunting more efficient and support content quality improvement.
Driving Force Behind Your Seamless Hunting Journey
Supported Platforms
Quick Hunt supports market-leading SIEM and EDR platforms. To overcome integration difficulties, parsing issues, and hunt on the log data that you have, a one-time configuration is required.
Start for Free

Community-Driven Threat Hunting
Backed by the SOC Prime Threat Bounty Program of nearly 400 researchers and the global community connecting cybersecurity professionals from over 6,000 organizations who provide feedback on their hunting experience daily.
Try now
Privacy-Conscious Approach to Hunting
Quick Hunt is designed following the industry best practices for data privacy protection. All hunting queries are launched during the existing browser session in the user local Data Plane and are not sent to the Quick Hunt server side.
SOC Prime applies the world-class encryption standards for maximum data security. The AES-256 encryption algorithm ensures the data is secure at rest, while the TLS 1.2 encryption protocol is used for encrypting data in transit. Quick Hunt doesn’t collect any PII when receiving user feedback.